Scoping
Scoping out a CUI Program
Scoping is a main component of any compliance program, as it provides the boundary of compliance.
What kind and what level of CUI is going to be handled
- How is the CUI going to be received and/or generated?
- How is the CUI going to be processed
- Who needs access to the CUI
- How are results going to be shared with their sponsor?
Use a science DMZ specialized for complex research systems with fast data transfer.
Keeping systems current in research is a challenge all institutions are facing. Use risk management to reduce impact
Determine Workflow
- Is your office space fit for controlled research?
- Are you going to use controlled software? Can you use shared systems?
- Are you working with other teams at another university?
- Who is going to help you stay secure and compliant?
- How are you capturing/generating data?
- Will you deal with a controlled thesis submission process?
With a controlled research project, using personally owned equipment is not recommended. Consider utilizing central facilities for research computing or data storage. Have IT provide managed laptops or desktops.
When using a secure drop site, ensure the service is authorized to store CUI.
It is important to consider the potential for meetings to be overheard. Consider finding a private meeting space.
These are all things to consider while determining workflow, and how you will take on your CUI project.
Cyberinfrastructure
Access to Systems and Data
Determine the type of access level required for the research team before access is granted. Create clear data boundaries between public, sensitive, and restricted research data.
| Access to Fundamental Research (published and shared broadly within research community) |
| Access to Sensitive Research (Non Personal Data / De-Identified Data) |
| Access to Restricted Research (Health Care or Student Data) |
| Access to Export Controlled Research (Government regulated technology, Defense non-classified related data such as ITAR, EAR, CMMC) |
| Access to Classified Research |
Remote Access to Data
- Remote access should never be allowed without establishing a VPN connection via a dedicated VPN profile for CUI
- User and Admin VPNs should be separate. Never provide a user with an Admin VPN
Organize Access to Data
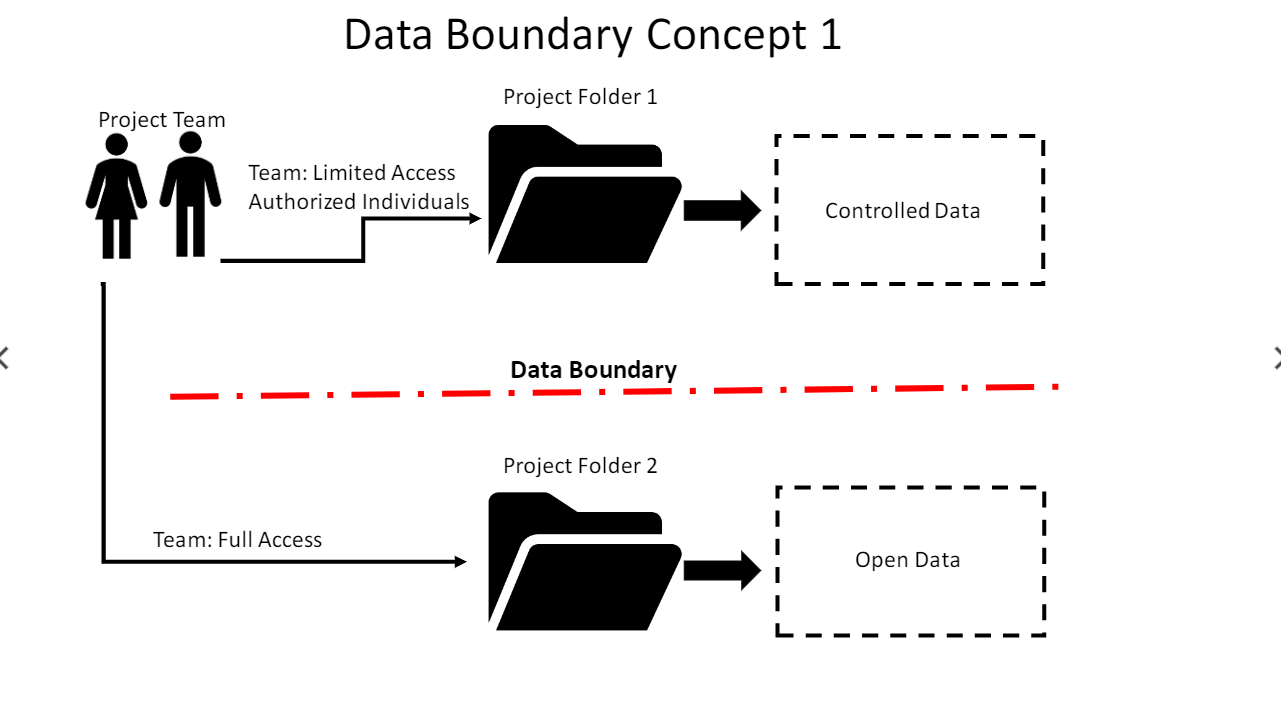
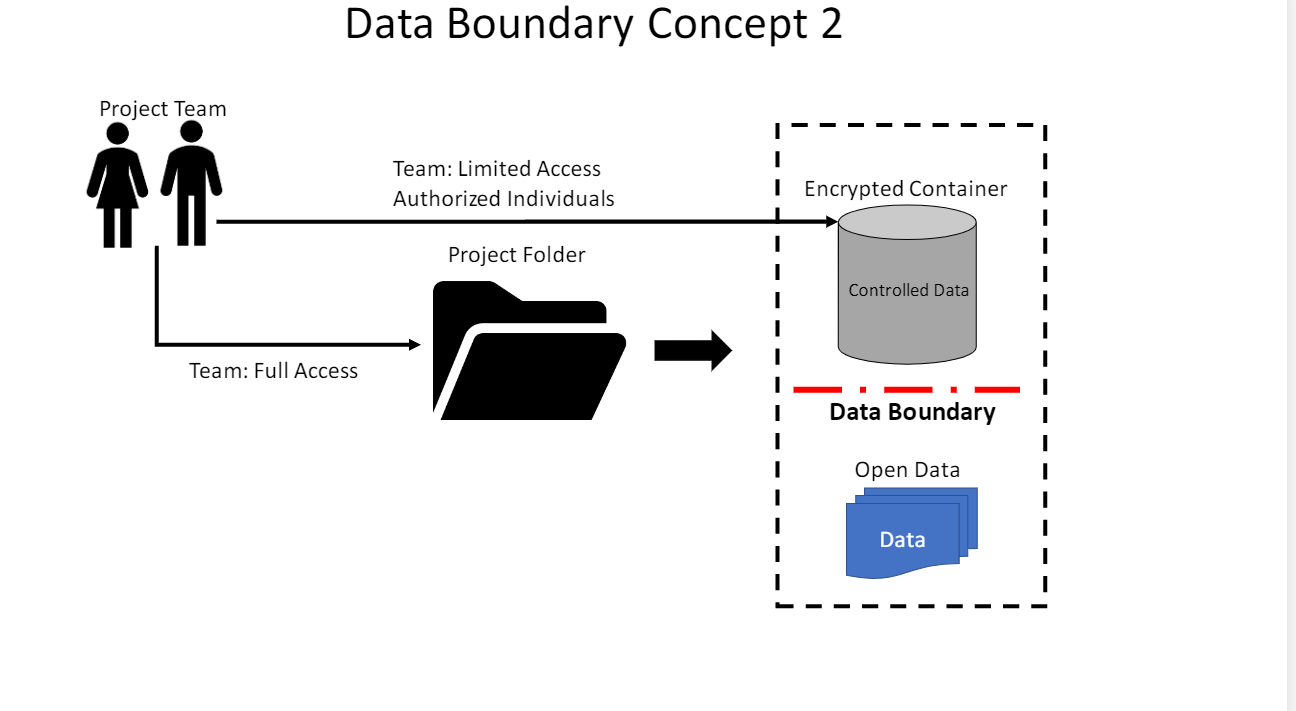
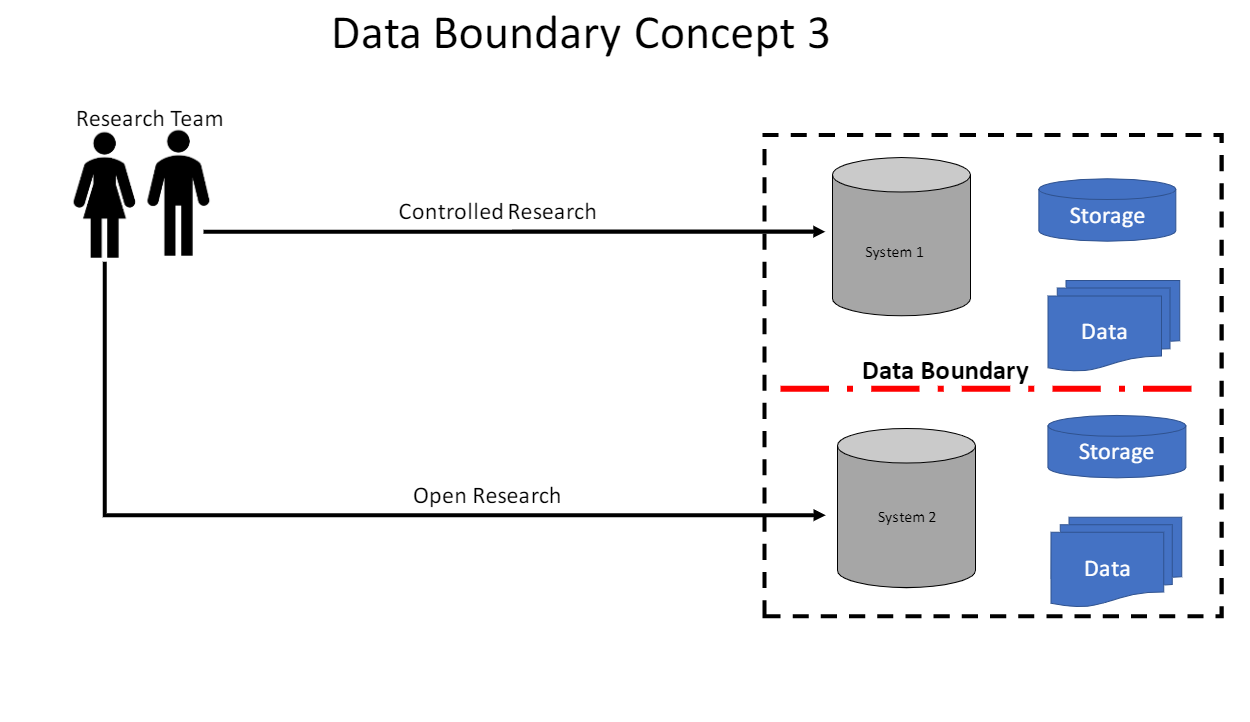
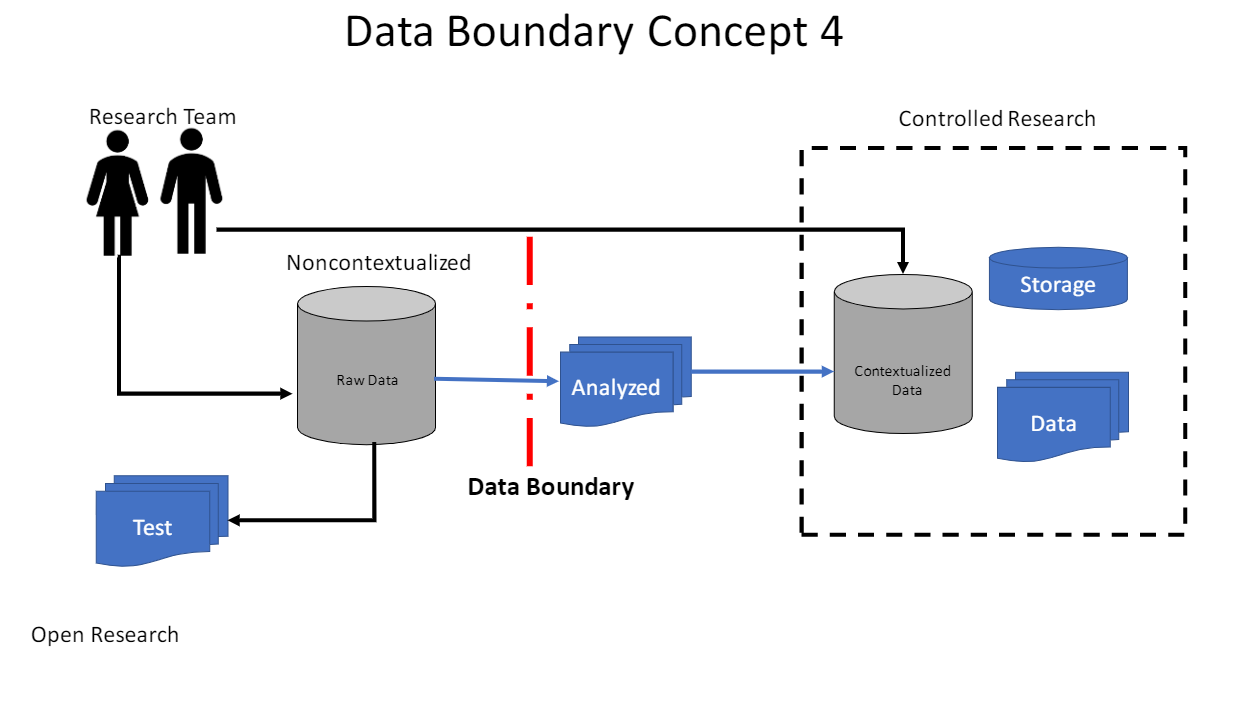
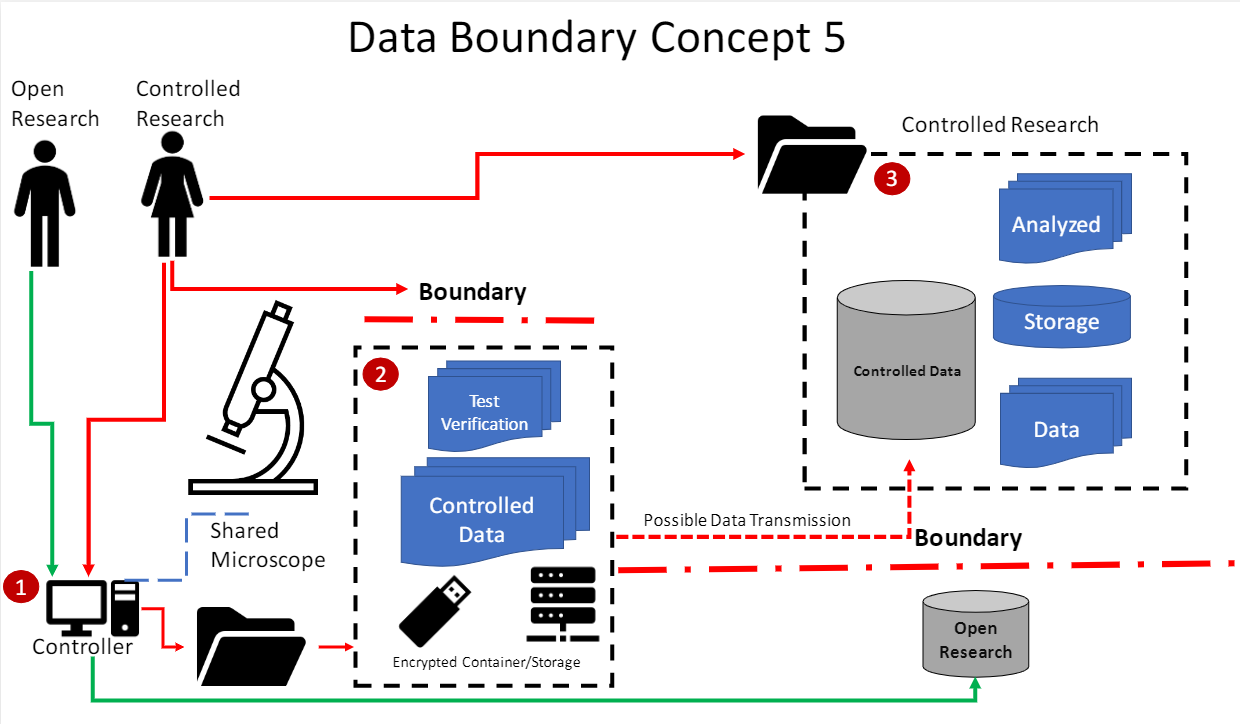
Organize data in a way that only authorized individuals have access. This will be a Data Boundary. An IT team should be able to help understand when the data becomes in scope of a given regulation.
Keep controlled research data separated from open research data.
Some data may be subject to marking requirements.
Here are some Data Boundary Concepts:
This work is supported by the National Science Foundation under Grant No. 1840043. Any opinions, recommendations, findings, or conclusions expressed are those of the author(s) and do not necessarily reflect the views of the National Science Foundation.
